Dylan Carroll
soc-galaxy.com
The majority of malware before 2020 has been created in Assembly or compiled languages like C, C++, and Delphi. Recently an increased amount of Python malware has surfaced, with a low barrier to entry, massive library collection and rapid development it is attractive to developers around the world, including malware authors.
Using libraries Py2exe or Pyinstaller Python scripts can be easily turned into standalone executables capable of running on Windows machines.
Malware written in Python has some distinct features, for one its file size and processing power are much greater than compiled malware in C. Python executables are usually at least 15MB and require more CPU and RAM usage as it is an interpreted language. And if the infection does not use a Python executable, then they are relying on Python being installed on the workstation or they will attempt the install as part of the infection.
In this article we will be showcasing a sample of a windows based Python info stealer that integrates into a discord server for exfil. I will showcase methods to detect this malware as well as detection techniques organizations can use to help detect and prevent such malware.
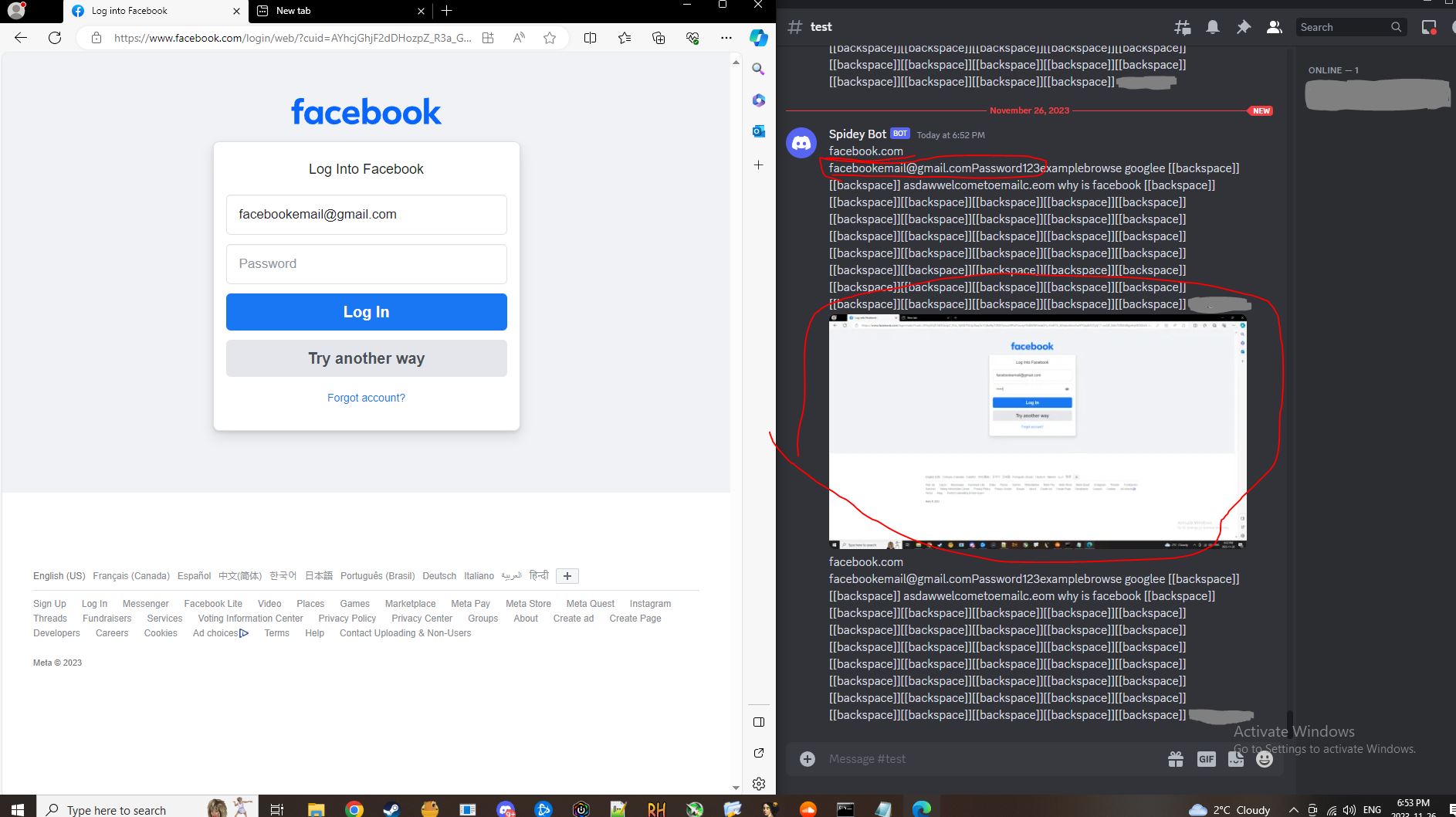
In the image above I log into Facebook on the left tab, and on the right tab the discord server the malware is set to use captures the username and password I type, as well as a screen shot to top it off. In random intervals it uploads everything I have typed as well as a screen shots.
Now that I know the malware is active as I have set it to exfil to my own discord server from my environment, I have brought in the sysinterals suite(NOTE some malware can detect these files and will cease execution, basic tricks like renaming them or slightly modifying the hash can sometimes counter these techniques).
The first thing I looked at was procexp.exe. Process explorer (procexec.exe) lists the currently active processes with a DLL mode to see DLLs and memory-mapped files loaded by processes. You can use this with command line enabled to see what started processes as well as Virus Total enabled to automatically upload the hashes of processes to label them with their ratings if they are already on Virus Total.
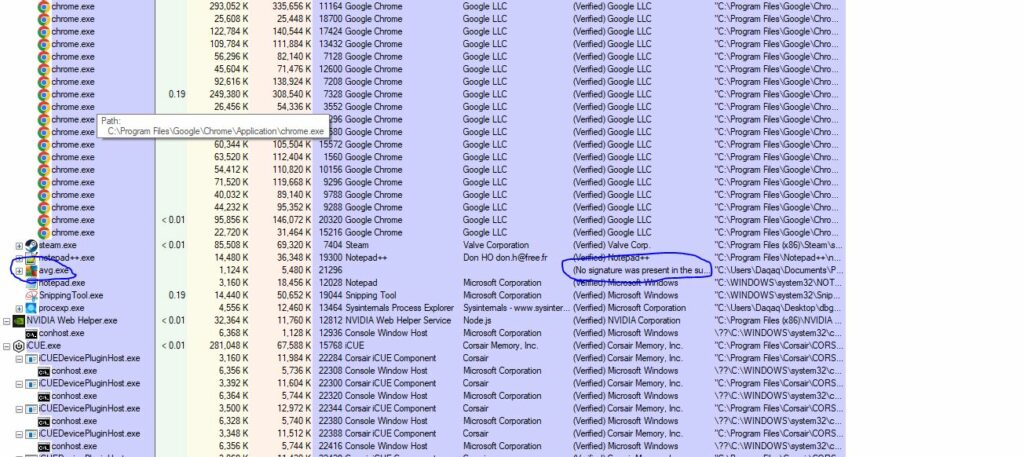
I noticed a file called avg.exe, and when you google this the results mention components of AVG Internet Security for Windows. Often if this was a real file from AVG that is a parent process, it should probably be signed. Turning on the Signing tool I can see that there is no signature present in the subject, and from the command line column that it was executed from a .lnk file. I found this to be very odd.
You can view strings after right clicking on file and going to its properties.
Interesting Strings found:
mss.screenshot: mss is a library in python to take screenshots and save them to png files.
random: Often seen in Python malware to generate random values used to add jitter / inconsistencies to communications.
There were also many strings related to the registry present, so that is the next area of focus.
Next up I am going to use autoruns.exe to show all the applications set to auto-start. Since malware usually is persistent on infected devices (will remain after restarting) you have a chance of finding how it is restarting itself using methods such as autoruns. When running autoruns a simple and surprisingly common place for malware to obtain persistence is using run or runonce registry keys. These registry keys execute the entries upon computer start up.
Upon looking at this field in autoruns.exe I noticed an anomaly.
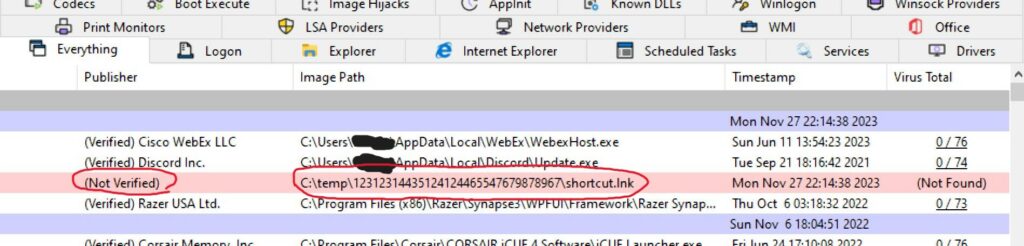
An entry exists pointing to a shortcut named shortcut.lnk stands out for its suspicious file path, usage of a shortcut and not having a verified publisher.
When you right click a shortcut you can select ‘show file location’ for a quick way to check what its pointing at. This takes us back to the originally detected file – avg.exe.
If you do not have fancy tools to do analysis at this point, sigcheck.exe can provide a quick and simple analysis.
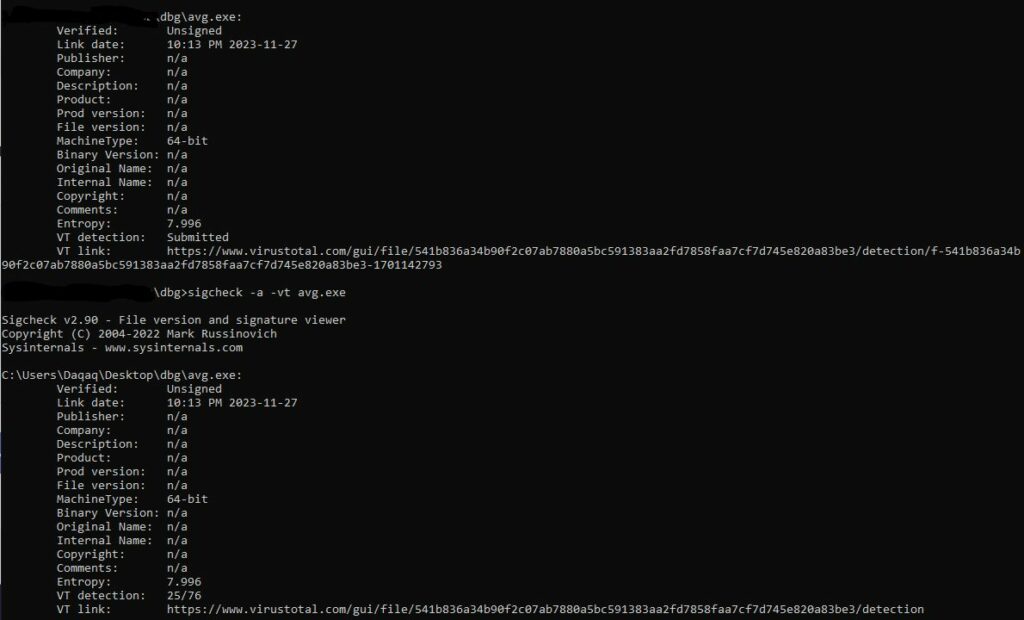
First I run sigcheck -a -vs avg.exe to check the file for its signature and upload it to virus total, then I use vt the next time after waiting a bit for the submission to finish. Now that this is submitted it should help security vendors detect this specific type a bit better, and we can see a large amount of detections, especially for Python malware, as well as no signature.
Although more simple than some malware, this Python Info Stealer does the job and can bypass some EDR tools to do its irregularities.
This combination of effective AV bypass with ease of creation may be part of the explanation to the increase Python malware.
Upon request rules written for specific tools can be provided to hunt for similar malware.
Some features to hunt on:
Python interpreter bundled in executables.
File types capable of starting executables or scripts in Run or Runonce.
Combination of Python Dependency files(.pyd) – for example Python library mss, and socket hint at screen shots and network communications within one Python executable.
Keyboard hooks from unsigned executables.
Large uncommon executables.
